Best Practices for Using Role-Based Permissions
By Karen Howe, Director of Training at Contract Logix
Protecting your sensitive contract data while providing adequate access to those who need it requires a flexible and easy-to-administer approach to role-based permissions.
A key feature of every contract management system should be the ability to provide a centralized and secure contract repository. But just because all your contracts live together in the same electronic storage location doesn’t mean all users should have equal access to all contracts. Nor should all users be able to perform the same tasks. Some sort of permission-based approach is needed. Here are some best practices for implementing role-based permissions.
Download An Introduction to Contract Management Software eBook to learn more.
Identify Your Security Requirements
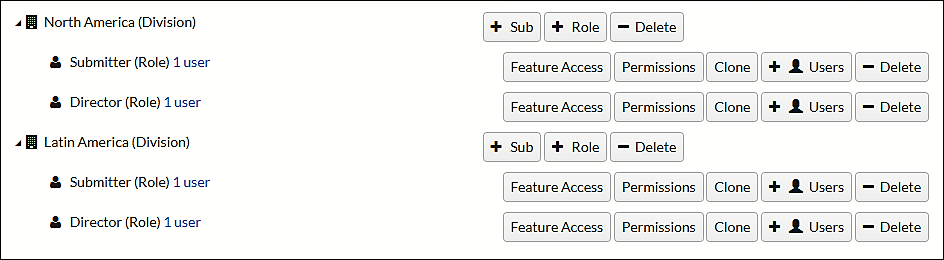
If you don’t have a clear picture of who needs access to which contracts, you can’t effectively create the proper roles and permissions. Clarification might begin by itemizing the types of contracts you manage. Will you be tracking Employment contracts (or other extremely sensitive documents) in the system? If so, it’s likely that only Human Resources and a few select others should have access to them. Or maybe your organization is segmented into separate business units, each having jurisdiction over their own contracts. In that case, you may want to create roles that only give users access to contracts in their own division or department.
A truly flexible system will enable you to configure access and permissions in a variety of ways. For example, with Contract Logix’s contract management software you can define a role having access to one or many contract types and then place that role within the organizational hierarchy, effectively restricting them to contracts owned by the sub-organization to which their role belongs. And for certain users whose needs transcend the department/division restriction, multiple roles can be assigned.
Know Your User Base
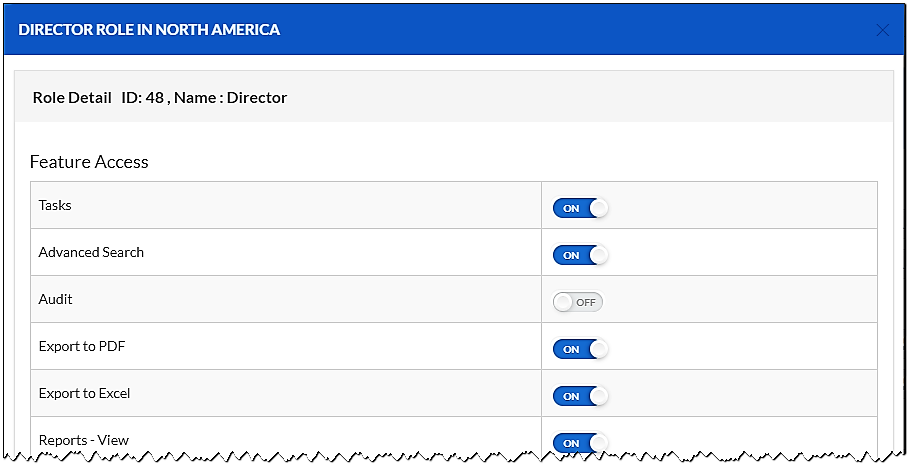
There’s more to role definition than deciding which contracts users can access. There’s also the question of what a user can DO in the system. Broad definitions like “end user” or “power user” are a good starting point (and Contract Logix supplies these “template” roles as part of the out-of-the-box system), but it’s inevitable that you’ll need to take a more granular approach. Posing questions like “Will these users be able to edit documents?” or “Can these users terminate a contract?” will help you clarify what roles you need.
Understand the Capabilities of Your Contract Management Software
Unless you understand how access to contracts and features is controlled in your contract system, you won’t be able to make informed configuration decisions when it comes to roles. You need to make sure your needs are aligned with how the role permissions are handled in whatever software you choose.
Contract Logix has a simple user interface for assigning permissions and the ability to clone existing roles and drag to any level in the organizational hierarchy. This makes it easy to implement and perhaps even more important, easy to adjust as needs change over time.
Keep it Simple
It’s tempting to construct an elaborate role-based security arrangement with a multi-tiered organizational hierarchy and roles having umpteen variations of permissible feature sets. Remember though, just because you can… doesn’t mean you should! Take into consideration the costs in time and effort that come with extremely complex solutions and only implement what you truly need to protect your valuable contract assets.
Takeaway
Whether you are a small company or a large organization, the key to effectively implementing role-based permissions is really knowing what contracts you have, who needs access to them, and how to leverage the strengths of your contract management software.


